Nmap (short for Network mapper) is a network scanning tool created by Gordon Lyon in September of 1997. It’s a powerful open-source tool used for network exploration and security auditing. It allows users to discover hosts, services and open ports on computer networks, aiding in the identification of vulnerabilities and potential security risks. Nmap works by sending packets to the target network and analyzing the responses, providing valuable information about the network’s topology, active hosts, and available services.
Kali Linux comes pre-installed with Nmap, so I won’t go into the installation process here. If you don’t have Nmap installed on your machine, go ahead and use your local package manager to get it installed if your using Linux. Otherwise, visit the official Nmap page for download links.
With Nmap installed we can get started. Given Nmap’s extensive capabilities, I might end up breaking this up into multiple parts. For now, I want to focus on the top ten scan types, their purpose, how they work and what the command for each of them is.
Ok lets get started, shall we?
TCP SYN Scan (Half-Open Scan)
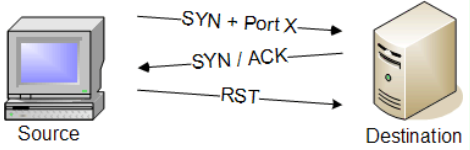
Purpose: Stealthily discovers open ports without completing the TCP handshake.
How it works: Initiates a connection to the target’s ports by sending SYN packets without completing the TCP handshake.
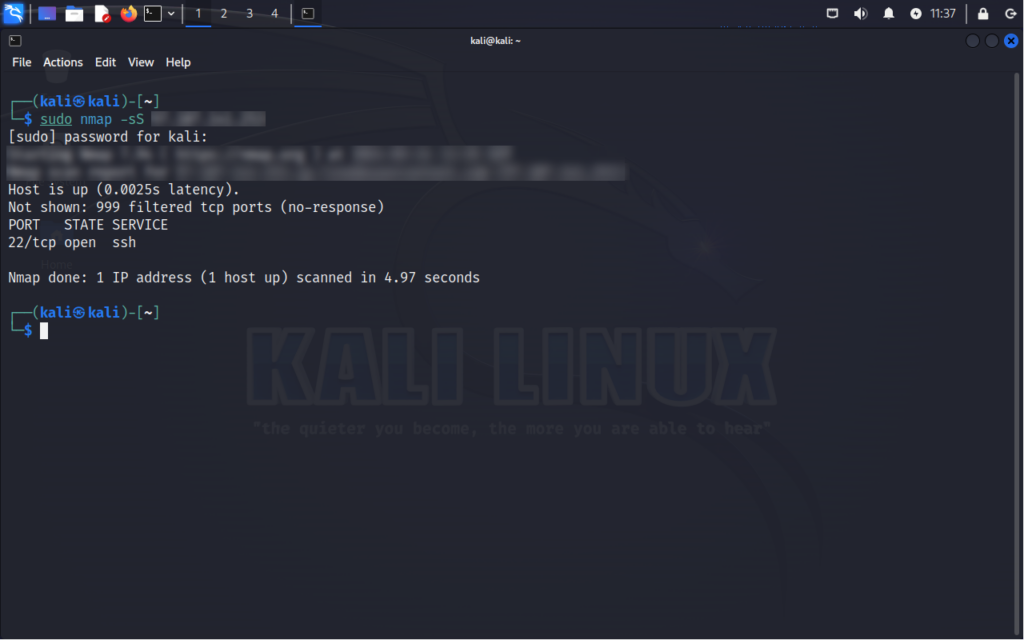
Command:
nmap -sS
TCP Connect Scan
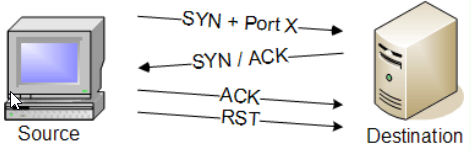
Purpose: Actively connects to target ports to determine their state.
How it works: Actively connects to target ports by completing the TCP three-way handshake.
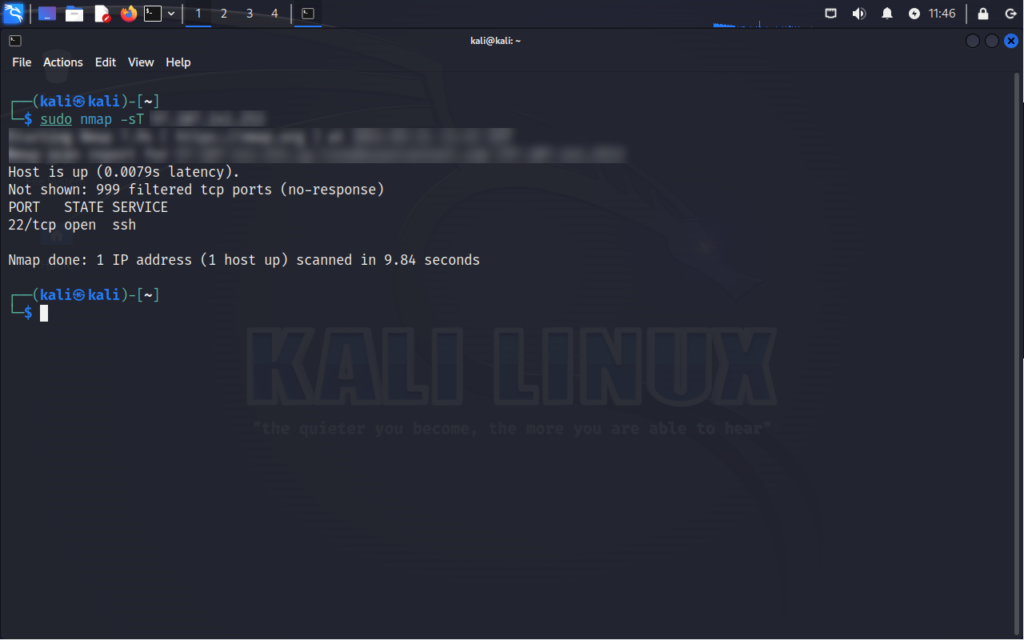
Command:
nmap -sT
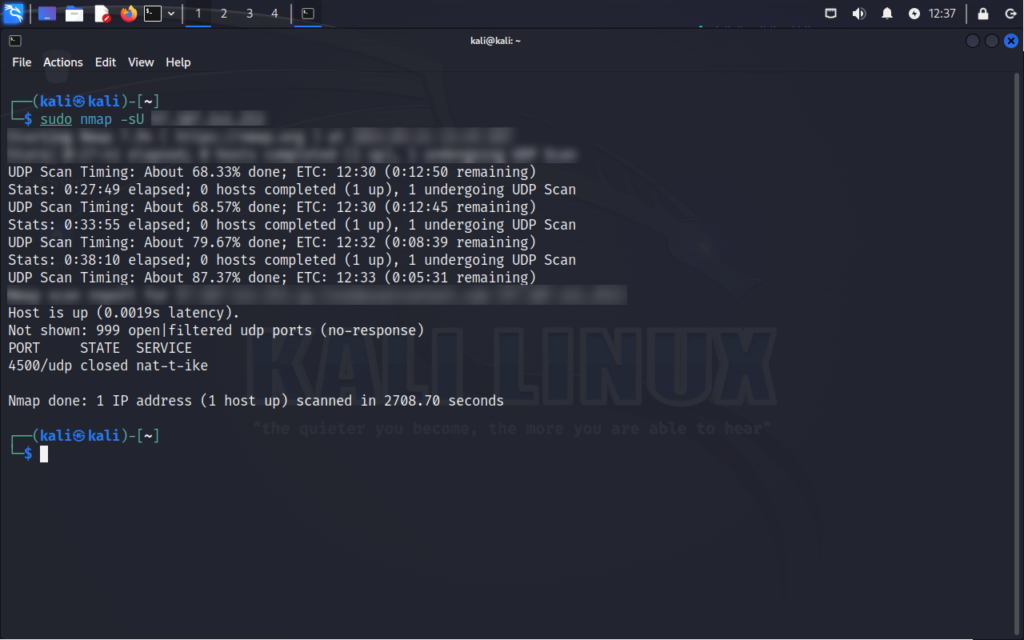
UDP Scan
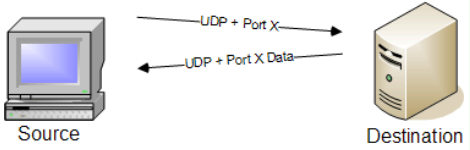
Purpose: Identifies open UDP ports and services running on them.
How it works: Sends UDP packets to target ports and analyzes responses to discover open ports.
Command:
nmap -sU
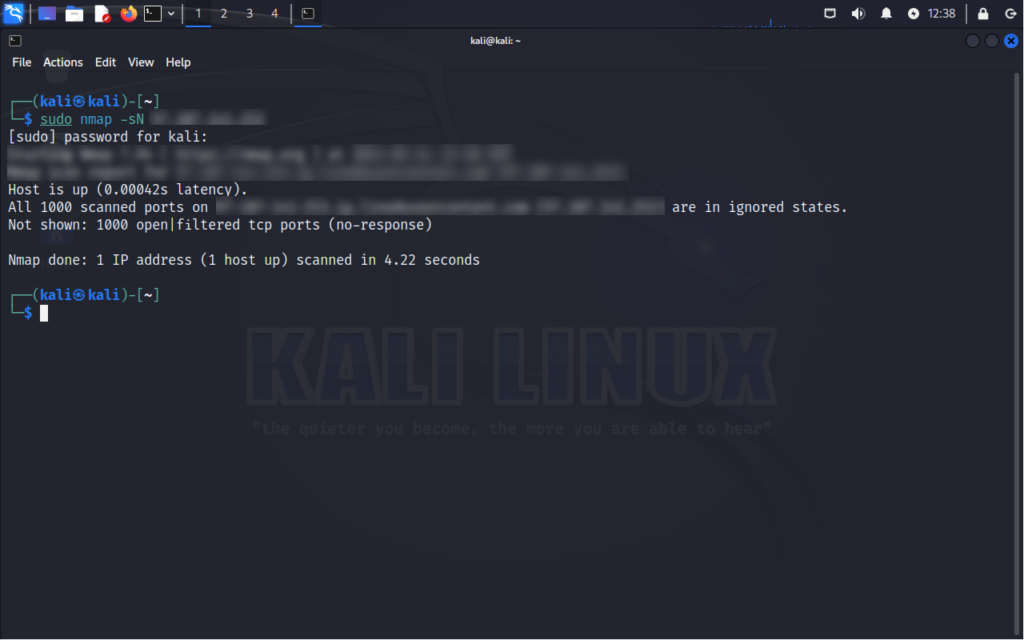
TCP NULL Scan
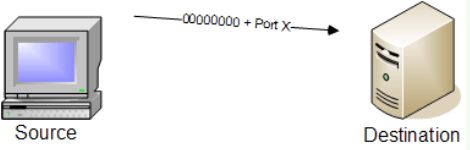
Purpose: Detects open ports by sending TCP packets with no flags set.
How it works: Sends TCP packets with no flags set to target ports, relying on how the target system responds.
Command:
nmap -sN
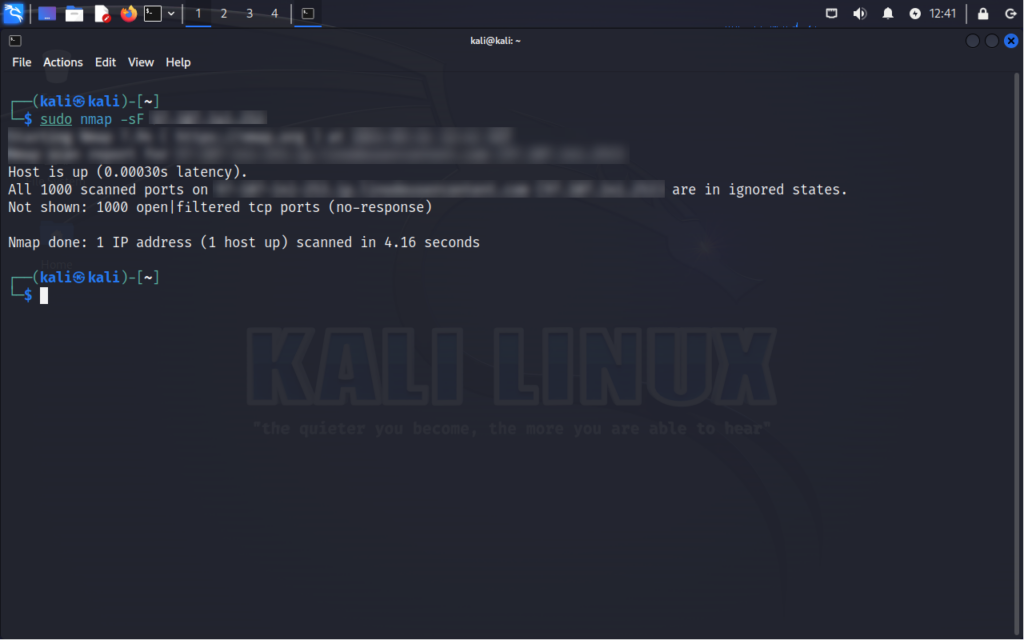
TCP FIN Scan
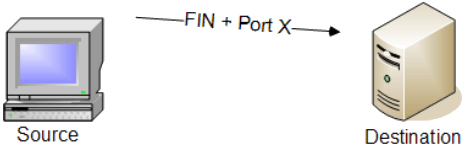
Purpose: Determines open ports by sending TCP packets with only the FIN flag set.
How it works: Sends TCP packets with only the FIN flag set to target ports, observing how the target responds.
Command:
nmap -sF
TCP XMAS Scan
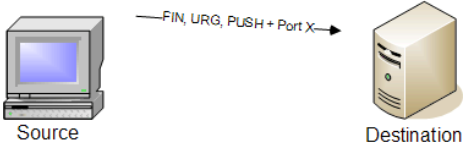
Purpose: Probes target ports using TCP packets with specific flag combinations.
How it works: Sends TCP packets with the FIN, PSH, and URG flags set to target ports.
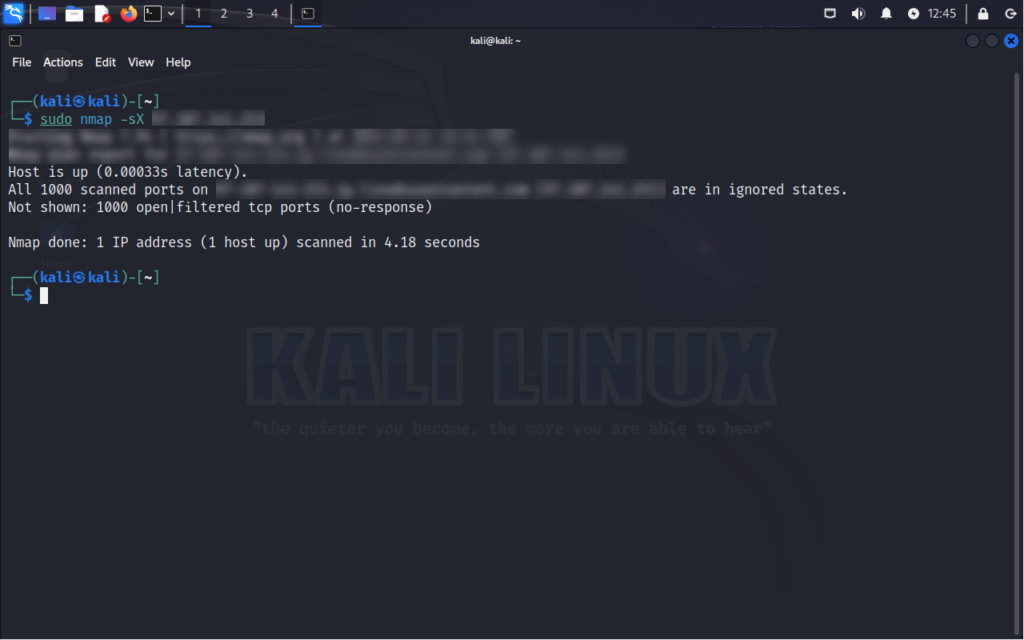
Command:
nmap -sX
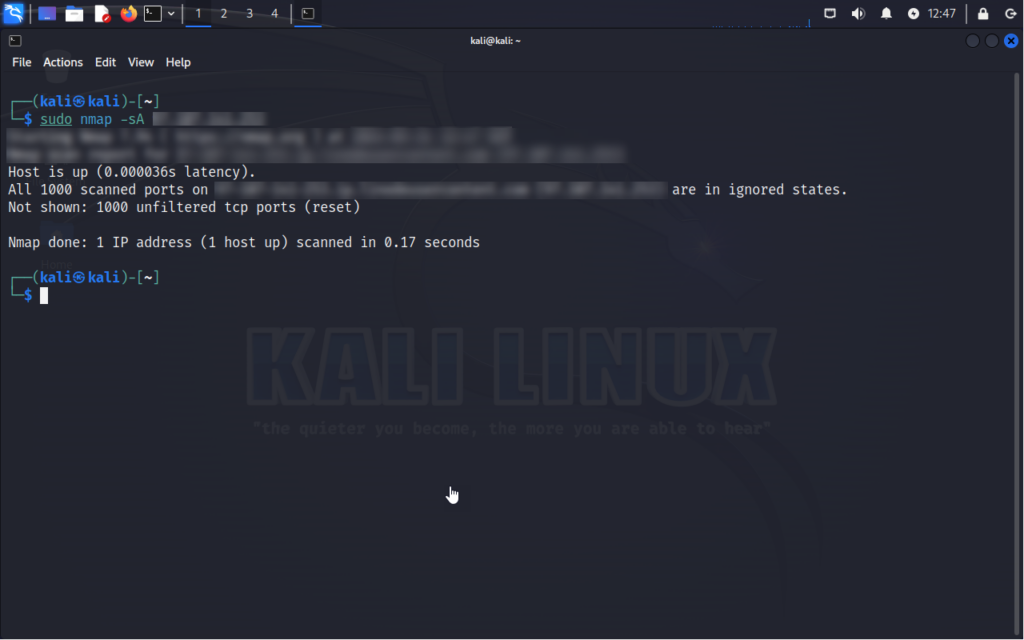
TCP ACK Scan
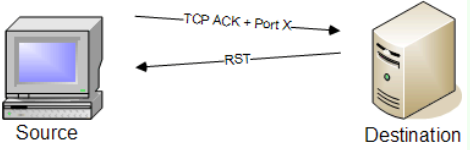
Purpose: Determines firewall rules by sending TCP packets with only the ACK flag set.
How it works: Sends TCP packets with only the ACK flag set to target ports, examining how the target responds.
Command:
nmap -sA
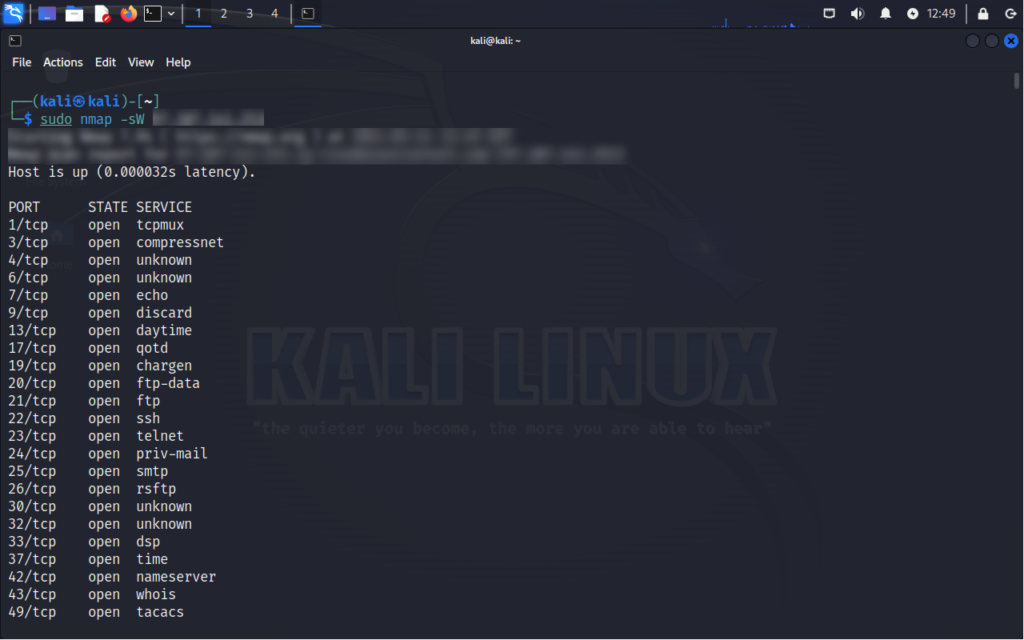
TCP Window Scan
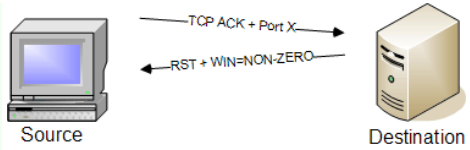
Purpose: Identifies open ports by analyzing the TCP window size in responses.
How it works: Explores target ports by analyzing the TCP window size in responses.
Command:
nmap -sW
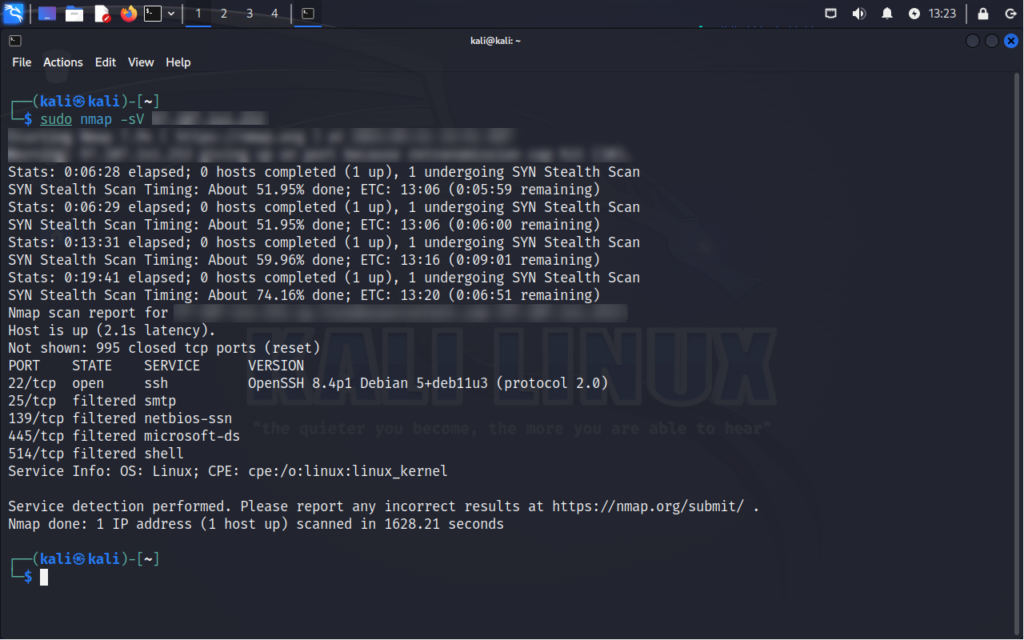
Version Detection Scan
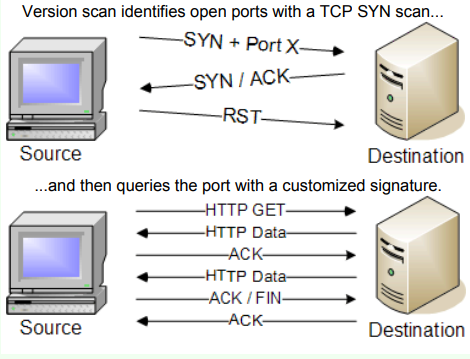
Purpose: Discovers the versions of services running on open ports.
How it works: Determines the versions of services running on open ports by analyzing their responses.
Command:
nmap -sV
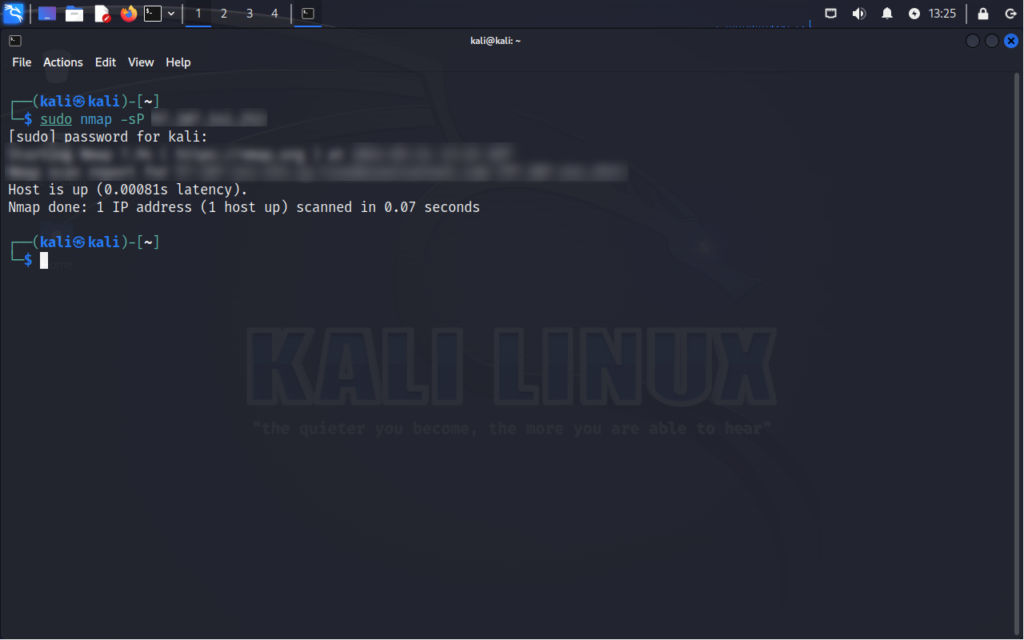
ICMP Echo Request Scan (Ping Scan)
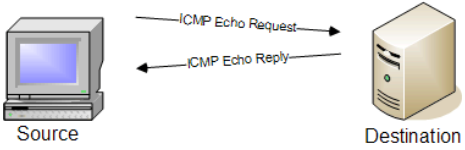
Purpose: Checks for active hosts on the network using ICMP echo requests.
How it works: Uses ICMP echo requests to determine if hosts are active on the network.
Command(s):
nmap -sP
nmap -PE
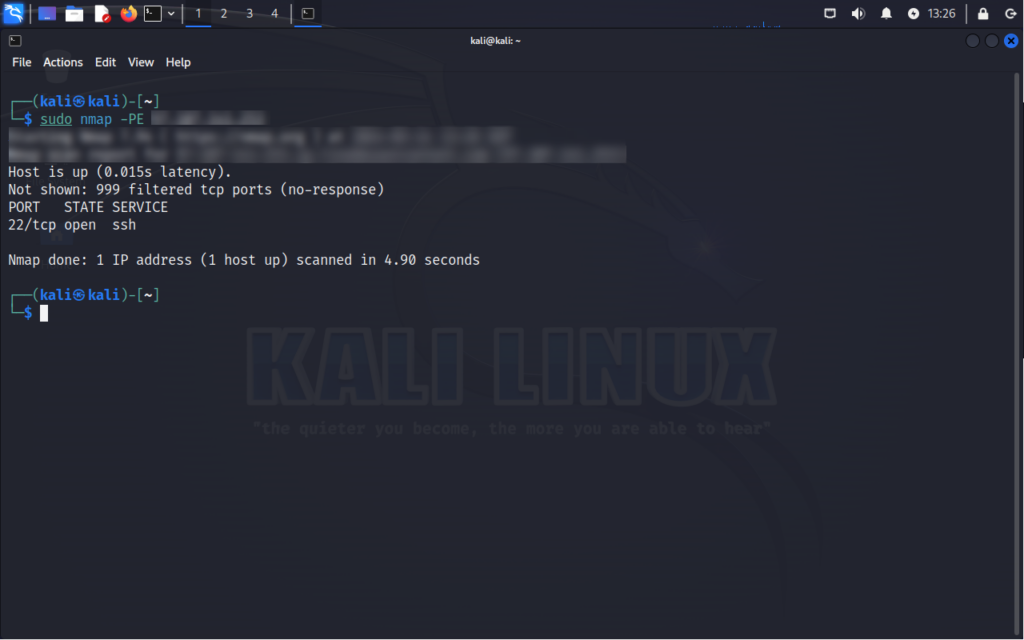
Well there you have it! This was a quick breakdown of some of the main scan Nmap scans. Like I mentioned before, I want to dive deeper into this in another post, maybe two.
In conclusion, Nmap stands as a versatile and essential tool for network reconnaissance and security auditing, offering a range of powerful scanning techniques to uncover vulnerabilities and assess network defenses. By mastering the various scan types and understanding their purposes, users can enhance their ability to secure their networks and systems effectively. Whether you’re a novice seeking to bolster your network security knowledge or a seasoned professional refining your skills, Nmap remains an essential asset in your cybersecurity toolkit.

