Ok so there’s Google, a powerful tool for acquiring information via the internet. But have you seen or heard of Shodan.io?
Shodan.io is a search engine for internet-connected devices and systems. Unlike traditional search engines that index websites, Shodan scans and indexes devices such as servers, routers, webcams, smart home devices, and industrial control systems. It gathers information like open ports, services running, software versions, and possible vulnerabilities.
This data is useful for security professionals to identify exposed or vulnerable devices on the internet, but it can also be used by malicious actors, making it a tool that requires careful and thoughtful use.
Shodan is free to use, but is limited in what you can do with a free account. Free accounts have limited search queries, reduced search results/filters and no API access. Shodan offers various pay models (mostly subscription-based), but they also provide a lifetime access account for $49. This is what I went with and it is more than sufficient for the type of searches I make. If you are doing many searches or are using this on behalf of your company, I would suggest checking out their pricing page and see what works for you.
Navigating to shodan.io, we are greeted with what looks like a normal search engine landing page. For the most part, it is just like your traditional search engine page (with some additional features, of course). There are tabs on the upper left-hand corner labeled: Shodan, Maps, Images, Monitor, Developer and More..
Here are the tabs and what their function is:
Shodan – This is the core search engine functionality of Shodan. It allows users to search for internet-connected devices using various filters and parameters, such as IP addresses, ports, geographic locations, software versions, and more.
Maps – Shodan Maps provides a visual representation of internet-connected devices around the world. By plotting devices on a map, users can quickly identify geographic clusters of specific types of devices or services, such as open databases, industrial control systems, or webcams. This tool is particularly useful for understanding the physical distribution of potentially vulnerable devices.
Images – The Images section showcases screenshots captured by Shodan from devices with web interfaces, such as security cameras, routers, or industrial systems. This feature provides a visual way to explore the kinds of interfaces exposed on the internet. It’s a powerful tool for identifying devices with weak security, like those with default login pages or outdated software interfaces.
Monitor – Shodan Monitor is designed for network administrators and security professionals who want to keep an eye on specific networks or IP ranges. Users can set up alerts to monitor their own assets, receiving notifications if new devices appear or if known devices change status. This feature helps organizations keep track of their attack surface and respond to new threats quickly.
Developer – Shodan offers an API for developers, allowing them to integrate Shodan’s data into their own applications or automation scripts. This is useful for security researchers and IT professionals who need to conduct automated scans, build custom dashboards, or integrate Shodan data into security tools. The API provides access to Shodan’s search capabilities, data streams, and other advanced functionalities.
More – This section encompasses additional tools and features that Shodan offers, such as: community, exploits, CLI and much more.
Let’s dive in and try out some searches!
"Cisco" port:23
Using the above search query we can scour the internet for devices manufactured by Cisco and have port 23 (Telnet) open. Here are some of the results:
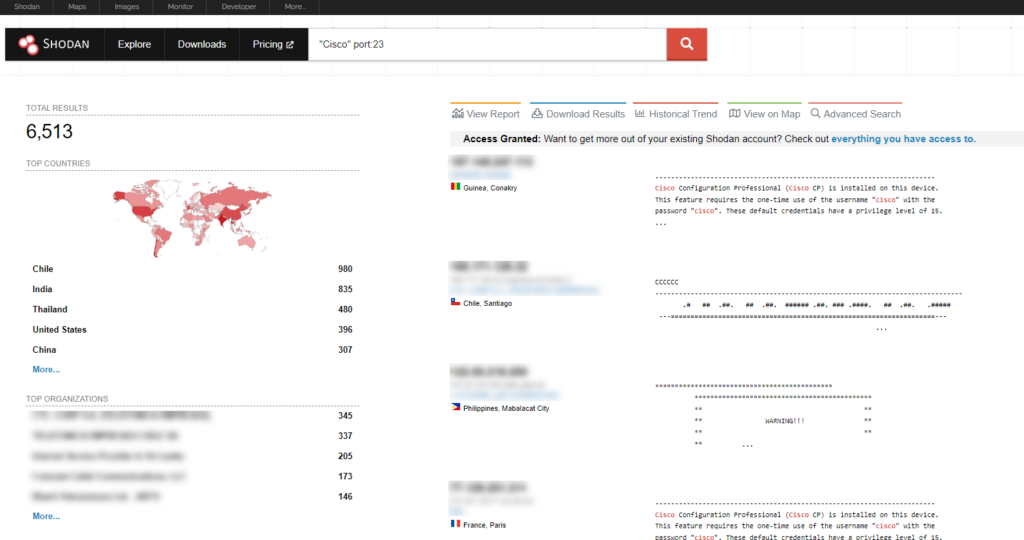
As you can see, utilizing this query allows us to get an understanding of the public-facing internet landscape of numerous Cisco Telnet-connected devices. Obviously, this is very bad, you never want Telnet open on any of your devices as it poses a major security risk.
Let’s do another search:
product:"OpenSSH" version:"7.5"Using this query we can find connected devices that are using OpenSSH version 7.5.
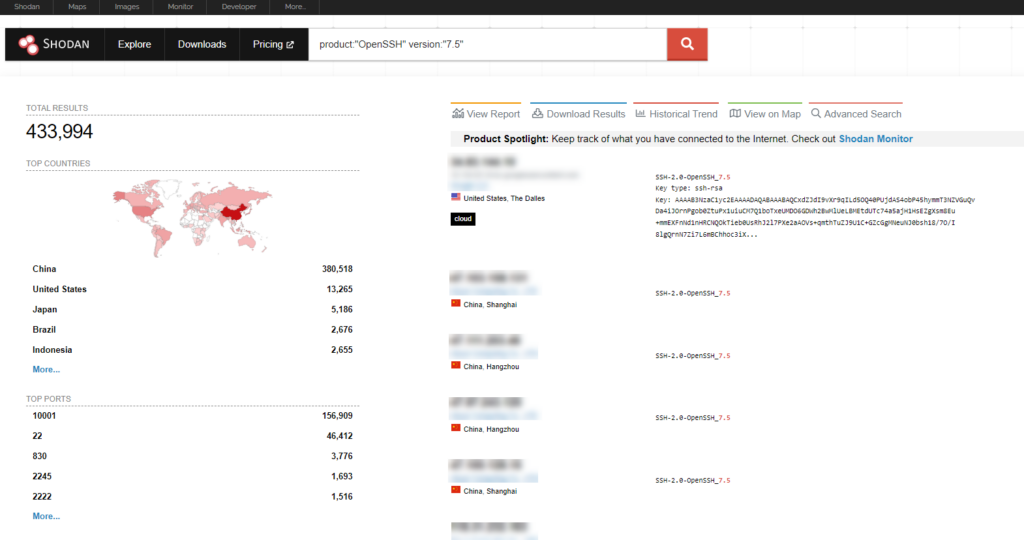
As you can see, we are presented with a list of connected devices using OpenSSH 7.5. Of course this is a very broad search and you would want to be a little more specific to narrow down your search range. Otherwise you will be stuck combing through mountains of output data.
The search options here are practically limitless, it all depends on your use-case and what type of information you are trying to obtain. Here is a list of some common search query examples:
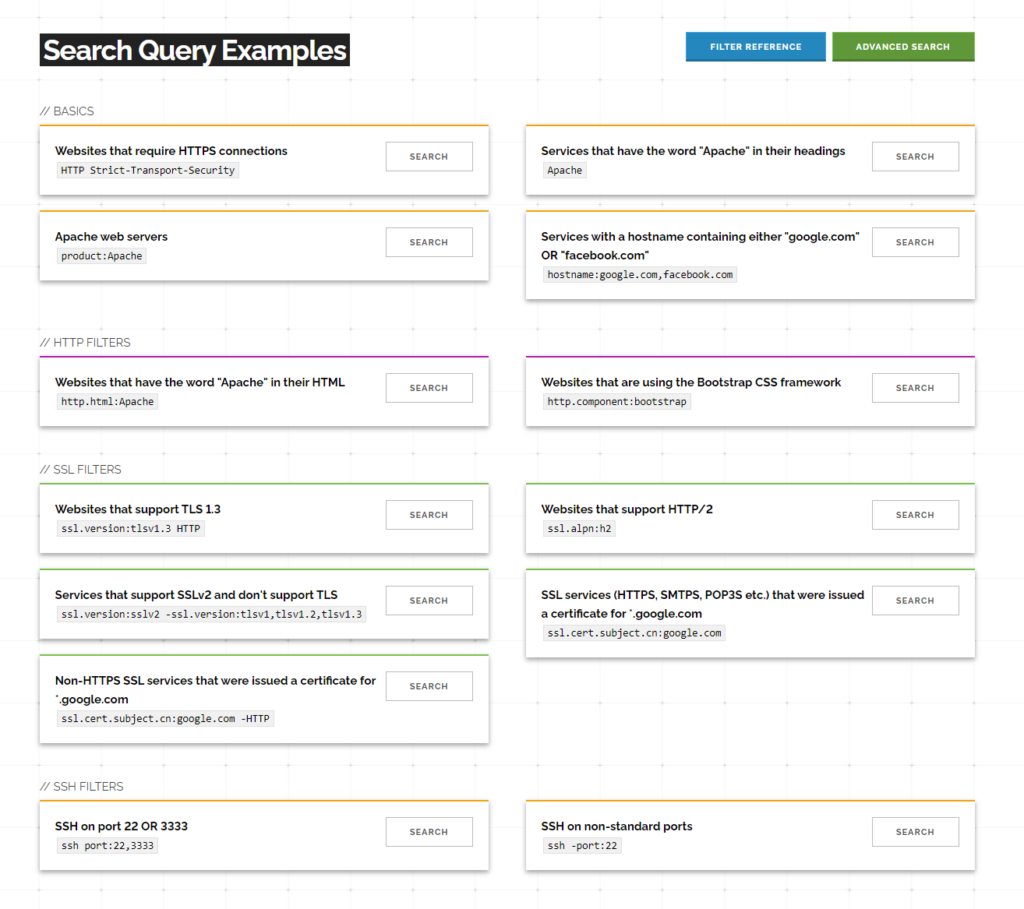
Feel free to visit Shodan’s Search Query Examples page for more. This page also includes the Advanced Search option which allows for a very specific search. This will also help you learn the search filter scheme. You can check out the Filter Reference page for more on that.
While we are on the subject of filters I wanted to bring up one other popular filtering method, that being screenshots. Shodan has a wide variety of screenshots available that were taken while Shodan was crawling/scanning the internet for these devices. You can use the Images tab (as seen below), or use one of the plethora of filters like so:
has_screenshot:true
screenshot.label:"Security Camera"
screenshot.os:"Linux"Please not that this is not a comprehensive list of filters, just a few that I knew off the top of my head.
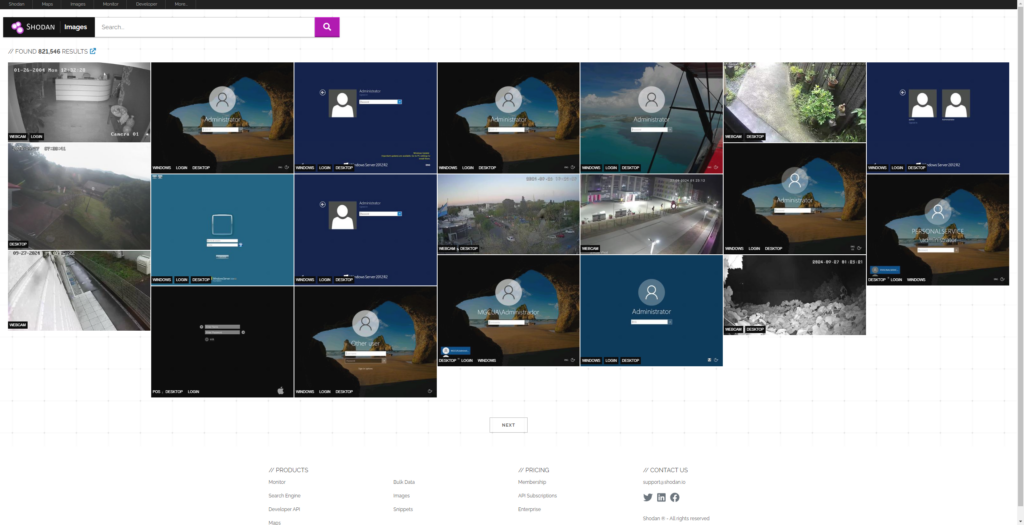
Here we can see some sample results from a basic search. We can see a bunch of RDP sessions shown in the screenshot above. A quick comment on the RDP sessions: These captures scraped by Shodan don’t have Network Level Authentication (NLA) enabled, hence the ability for Shodan to collect the screenshot. While the Microsoft RDP client enforces Network Level Authentication by default on the client side, it could be bypassed if the server doesn’t enforce it. A quick reminder here to read my disclaimer, but that goes without saying (I hope).
Shodan is a brilliant tool that offers so much in terms of providing visibility into our internet security. Often I find myself curious and taking a look at what I can find on Shodan. At times my main issue is coming up with a search topic, not finding the connected device. You can get lost for hours on this search engine. Today I was searching through Shodan and found this one funny connected device, so I’ll leave this post off with this:
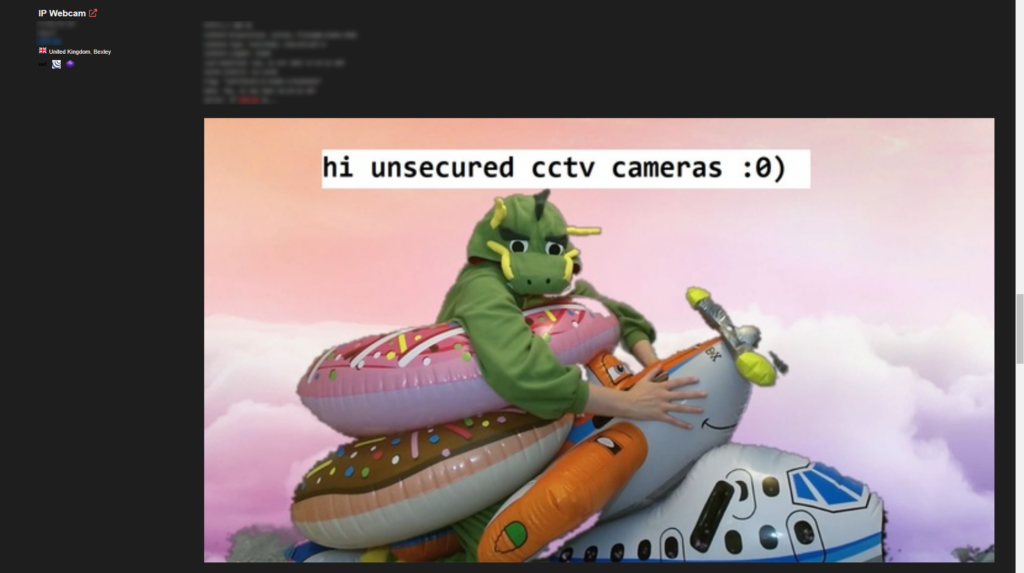
Enjoy! 🙂 Until next time folks!

