Welcome to this overview of the concept of Defense-in-Depth. This is a post I’ve been wanting to make for a while in preparation for my hardening guides. I was going to originally include this as a preface to my Windows hardening guide, but felt this deserved a post on its own. let’s jump right in and cover the concept of ‘Defense-in-Depth” or the “Swiss Cheese Model”.
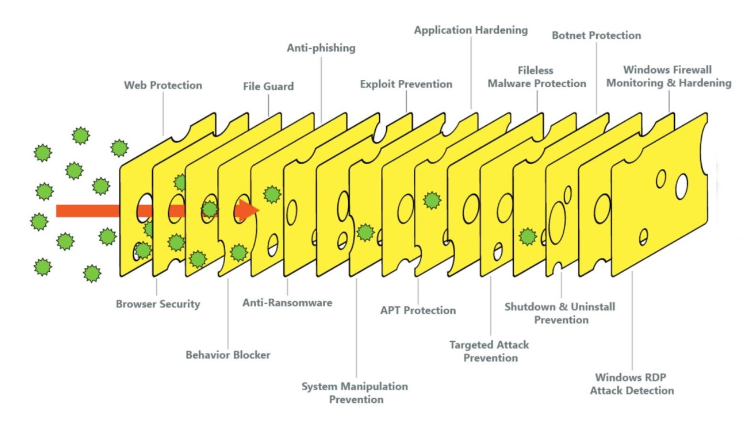
Defense in depth is a strategy that leverages multiple security measures to protect an organization’s assets. The principle behind this is that no single security product or strategy can fully protect a network from all attacks. Instead, this concept uses multiple layers of security to slow down an attacker and give defenders time to detect and respond to their attacks. Meaning if one system fails to protect your network, another will stop the attacker completely or slow them down enough to give you enough time to respond and remediate the threat.
Types of Security Controls
There are three main categories of controls in a Defense-in-Depth strategy: Physical, Technical (Logical), and Administrative.
Physical Controls
This is a very important aspect that I feel doesn’t get the attention it deserves at times. Of course it is much easier to compromise a machine if you have physical access to it (i.e. Stuxnet). This may not be as be of a risk to home users and to be honest if you have individuals breaking into your home, you probably aren’t thinking about your computers or mobile devices at first and for good reasons. But, for an enterprise environment physical controls can be everything.
Physical controls are measures designed to prevent unauthorized physical access to assets such as data centers, servers, and workstations. These are essential for safeguarding the physical infrastructure.
Examples of physical controls include:
Security guards – To monitor and protect physical locations.
Locks and access control systems – Man traps, electronic keycard systems, biometric scanners, or traditional locks and keys.
CCTV cameras – For surveillance and monitoring of sensitive areas.
Alarms – Intrusion detection systems to alert security personnel in case of breaches.
Environmental controls – Fire suppression, climate control systems, and UPS (Uninterruptible Power Supplies) to protect hardware from environmental hazards.
Technical (Logical) Controls
These are the type of controls most people are familiar with; you know, firewalls, AV solutions, EDRs, etc. These are the automated mechanisms that enforce security policies and protect an organization’s infrastructure.
Technical controls use software and hardware solutions to protect data, systems, and networks from threats. These controls are typically automated and require less human intervention than physical controls. They are often scalable and very effective when implemented properly.
Examples of technical controls include:
Firewalls – To filter and control traffic based on predefined rules.
Anti-virus and Anti-malware software – To detect, prevent, and remove malicious software.
Intrusion Detection/Prevention Systems (IDS/IPS) – To monitor network or system activities for malicious behavior and take preventive actions.
Encryption – To protect data in transit and at rest from unauthorized access.
Multi-factor Authentication (MFA) – To enhance identity verification through multiple authentication factors.
Network Segmentation – Dividing a network into smaller, isolated sections to limit access to sensitive information.
Access Control Lists (ACLs) – To restrict access to data and systems based on user roles or permissions.
Administrative Controls
Arguably this is the most important set of controls. Really?! Well, yes. Now why do I say that? The strongest (and weakest) link in security is the people. A well trained and vigilant user can halt a cyber attack that took months or even years to plan. According to many statistics such as CloudFlare’s recent report, over 90% successful cyber attacks start with email phishing and social engineering techniques. Attackers use deceptive links, malicious attachments, and brand impersonation to trick users into divulging sensitive information or downloading malware. This continues to be one of the biggest attack vectors and threat actors know this too. Now administrative controls aren’t all about training and awareness, but I wanted to highlight this very important part.
Administrative controls involve policies, procedures, and guidelines put in place to dictate human behavior and organizational practices. These are often designed to ensure compliance with security policies and to guide employees in safe security practices.
Examples of administrative controls include:
Security policies – Guidelines that outline acceptable use, data protection, and incident response procedures.
Training and awareness programs – Educating employees on security best practices and recognizing threats like phishing.
Incident response plans – Procedures for dealing with security incidents to minimize damage and recovery time.
Regular audits and risk assessments – Ongoing reviews to ensure compliance with security policies and identify potential vulnerabilities.
Access control policies – Defining who has access to which systems and data based on job roles.
Common Security Elements Used in Defense in Depth
Defense in Depth incorporates a variety of security tools and techniques across its layers. Some common security elements include:
Anti-virus/Anti-malware software – To detect and remove malicious software.
Firewalls – To control incoming and outgoing network traffic.
Network Segmentation – Isolating critical systems from less secure areas of the network to minimize the spread of attacks.
Intrusion Detection Systems (IDS) – To monitor network traffic for suspicious activity.
Data Encryption – To protect sensitive information from unauthorized access during transmission and storage.
Security Information and Event Management (SIEM) systems – For real-time analysis and logging of security alerts from across the IT infrastructure.
Patch Management – Keeping software up to date to prevent exploitation of known vulnerabilities.
Backup and Recovery – Regular backups of data and systems to ensure continuity in case of an attack or system failure.
Access Control Systems – Role-based access, multifactor authentication, and user provisioning to ensure only authorized individuals can access certain resources.
Defense in Depth is important because no single security measure is foolproof. By layering security controls, organizations can reduce the likelihood of a successful breach and limit the damage if an attack occurs. Each layer should address a specific threat or vulnerability, ensuring a comprehensive defense against a wide range of threats.
Thanks for taking the time to get this far! Stay tuned to my future hardening guides for both Windows and Linux.

