PowerShell is one of the most powerful tools at a Security Analyst’s disposal. It’s built right into Windows and capable of pulling deep insights with just a few lines. It enables users to investigate systems, extract critical information and facilitate tasks during investigations. With PowerShell, analysts can search logs, monitor network activity, uncover persistence mechanisms, and gather forensic artifacts. Its flexibility makes it an essential tool for quickly identifying suspicious behavior and streamlining investigations.
Learning PowerShell is a key skill for anyone working in Cybersecurity. Below is a list of practical PowerShell commands I’ve compiled that can be found useful. I’ll break each one down and explain how it can be applied in real-world scenarios.
Get All Domain Users and Their Last Logon Times
Get-ADUser -Filter * -Properties LastLogonDate, Enabled |
Select-Object SamAccountName, Enabled, LastLogonDate
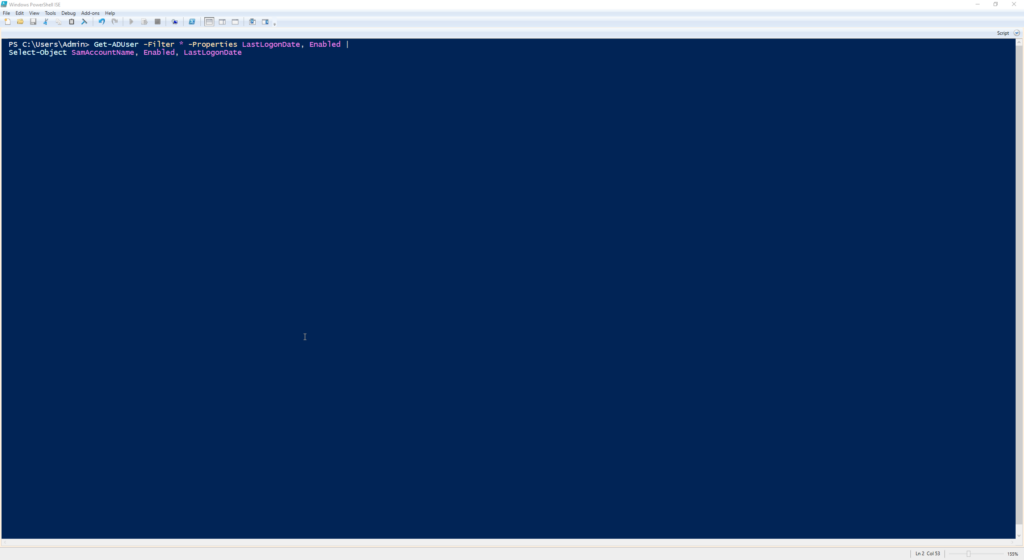
Use this to pull a full list of users from Active Directory, including their last logon date and whether their account is currently enabled.
- Useful for spotting stale, inactive, or potentially compromised accounts
- Helps identify accounts that may be enabled but unused, often leveraged by attackers
- Can be combined with filters to look for accounts that haven’t logged in recently
What It Does:Get-ADUser -Filter * – Queries all users in Active Directory.-Properties LastLogonDate, Enabled – Includes the last logon date and enabled status.Select-Object SamAccountName, Enabled, LastLogonDate – Displays the username, account status, and last logon.
List Startup Items (Run & RunOnce Registry Keys)
# Current User - Run
Get-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\Run"
# Local Machine - Run
Get-ItemProperty -Path "HKLM:\Software\Microsoft\Windows\CurrentVersion\Run"
# Current User - RunOnce
Get-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\RunOnce"
# Local Machine - RunOnce
Get-ItemProperty -Path "HKLM:\Software\Microsoft\Windows\CurrentVersion\RunOnce"
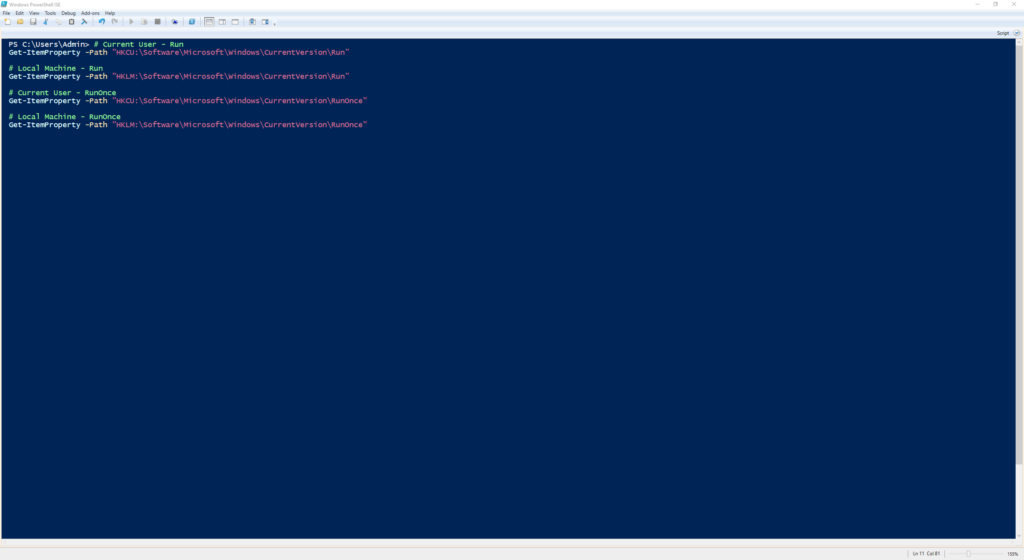
This reveals what programs are set to run at startup or on next login, both for the user and system.
- Helps uncover persistence mechanisms used by malware or unauthorized tools
- A quick way to audit potentially suspicious startup behavior
- Checks both one-time and recurring startup entries
What It Does:
Get-ItemProperty – Retrieves the registry values (startup entries) at the specified pathHKCU:\Software\Microsoft\Windows\CurrentVersion\RunHKLM:\Software\Microsoft\Windows\CurrentVersion\RunHKCU:\Software\Microsoft\Windows\CurrentVersion\RunOnceHKLM:\Software\Microsoft\Windows\CurrentVersion\RunOnce
Search for Logon Events (Event ID 4624 – Successful Logon)
Get-WinEvent -FilterHashtable @{LogName='Security'; ID=4624} |
Select-Object TimeCreated, @{Name='Account';Expression={$_.Properties[5].Value}}, @{Name='IP';Expression={$_.Properties[18].Value}} |
Format-Table -AutoSize
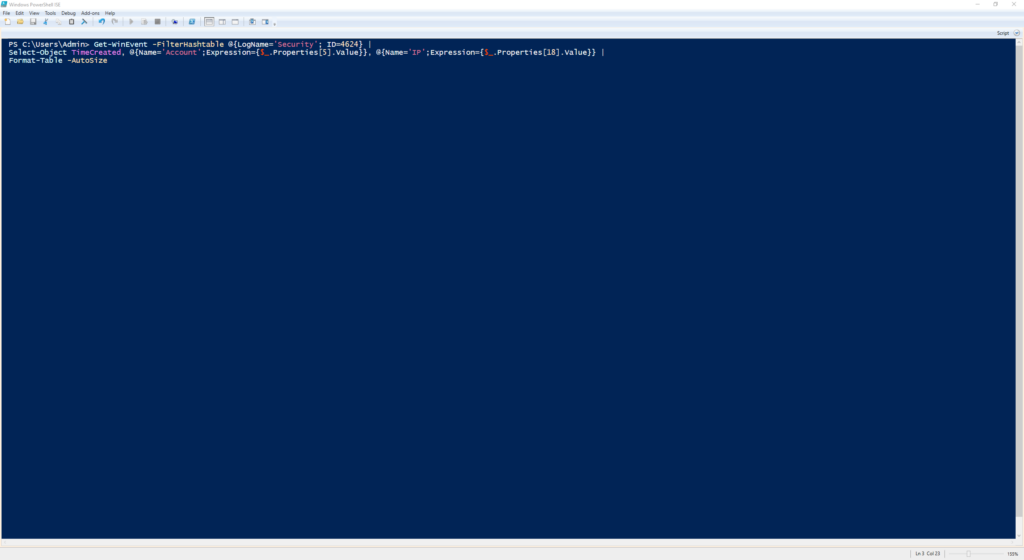
Displays all successful login attempts and where they came from.
- Great for investigating unusual login times or locations
- Useful in lateral movement detection or brute-force investigations
- Shows both the account name and IP address used
What it Does:
Get-WinEvent -FilterHashtable @{LogName='Security'; ID=4624} – Filters for successful logon events from the Security logSelect-Object TimeCreated, … – Outputs the event timestamp and custom fields@{Name='Account'; Expression = { $_.Properties[5].Value }} – Extracts the account name used for the logon@{Name='IP'; Expression = { $_.Properties[18].Value }} – Extracts the source IP addressFormat-Table -AutoSize – Neatly formats the output in a readable table
List Active TCP Connections and Their Processes
Get-NetTCPConnection -State Established |
ForEach-Object {Get-Process -Id $_.OwningProcess} |
Select-Object ProcessName, Id
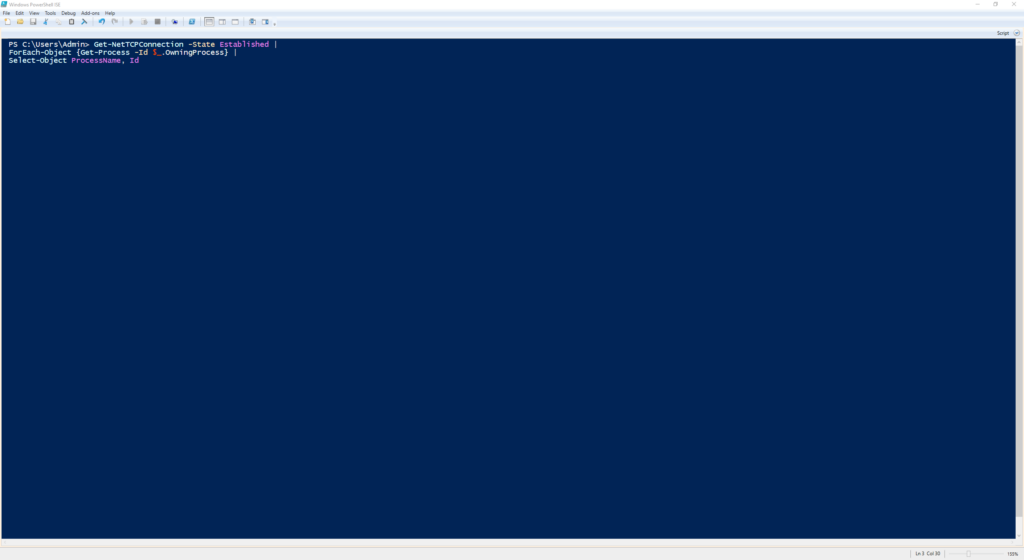
Shows all active TCP connections and the processes that created them.
- Useful for detecting unexpected network activity
- Maps open connections back to the parent process
- Can help detect malware beaconing or reverse shells
What It Does:Get-NetTCPConnection -State Established – Gets all established TCP connectionsForEach-Object { Get-Process -Id $_.OwningProcess } – For each connection, retrieves the owning process using the OwningProcess propertySelect-Object ProcessName, Id – Displays the process name and process ID (PID) for each connection
List Installed Programs
Get-ItemProperty @(
"HKLM:\Software\Microsoft\Windows\CurrentVersion\Uninstall*",
"HKLM:\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall*") |
Where-Object { $_.DisplayName } |
Select-Object DisplayName, DisplayVersion, InstallDate
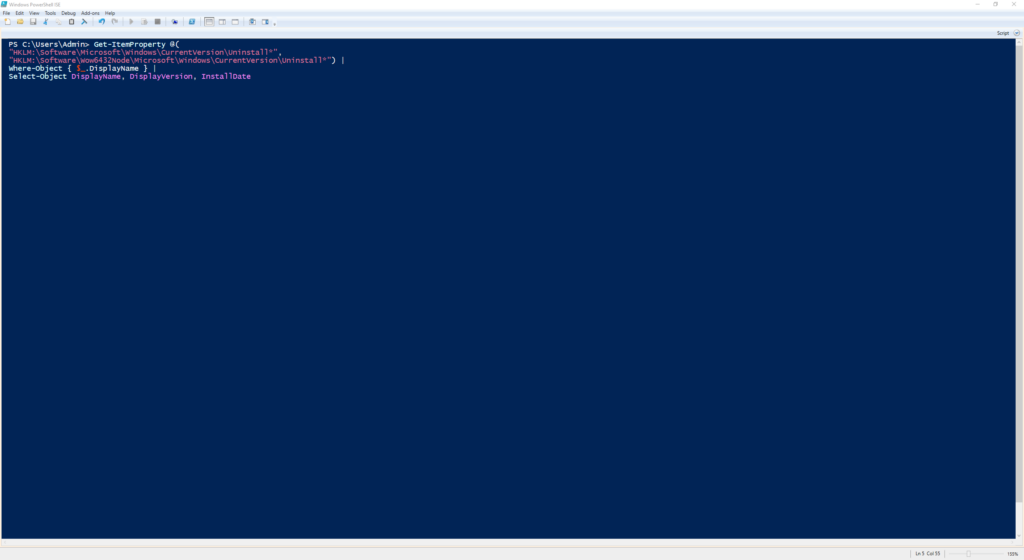
This command pulls installed applications from the registry, both 64-bit and 32-bit, including name, version, and install date.
- Useful for spotting suspicious or unauthorized software
- Helps verify software baselines during auditing
- Can be filtered by install date or name for fast triage
What It Does:Get-ItemProperty @(…) – Retrieves registry-based information from specified locationsWhere-Object { $_.DisplayName } – Filters out entries with no name (noise)Select-Object DisplayName, DisplayVersion, InstallDate – Shows program name, version, and when it was installed
Find Recently Created Files
Get-ChildItem -Path C:\Users -Recurse -File -ErrorAction SilentlyContinue |
Where-Object { $_.CreationTime -gt (Get-Date).AddDays(-3) }
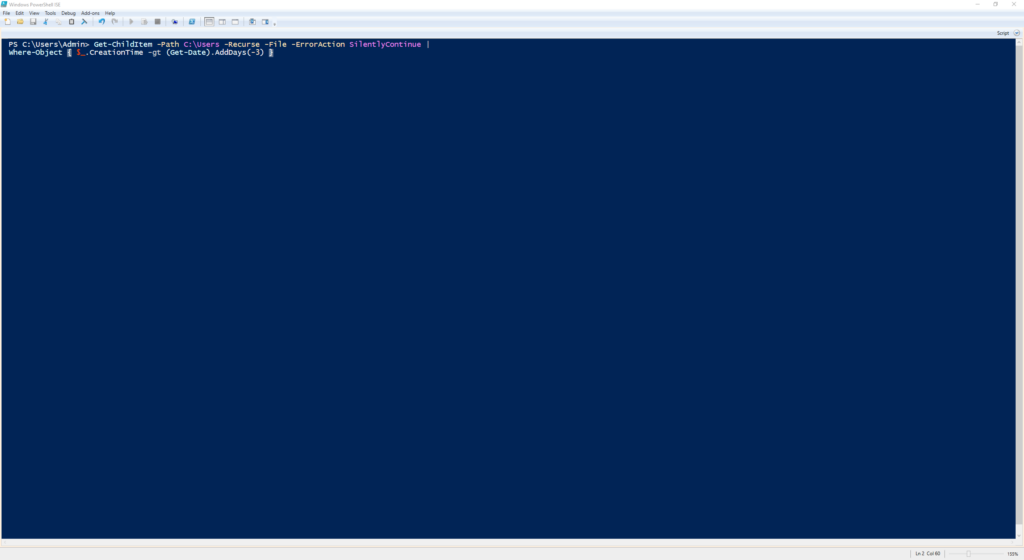
Searches through user directories for files created in the last few days.
- Useful for detecting payloads or dropped files post-compromise
- Helps track file activity during malware execution
- Works well after suspicious downloads or phishing attempts
What It Does:Get-ChildItem -Path C:\Users -Recurse -File – Scans all user directories for files-ErrorAction SilentlyContinue – Suppresses access denied messagesWhere-Object { $_.CreationTime -gt (Get-Date).AddDays(-3) }
Check for Malicious Scheduled Tasks
Get-ScheduledTask |
Select-Object TaskName, TaskPath, State, Actions |
Format-Table -AutoSize
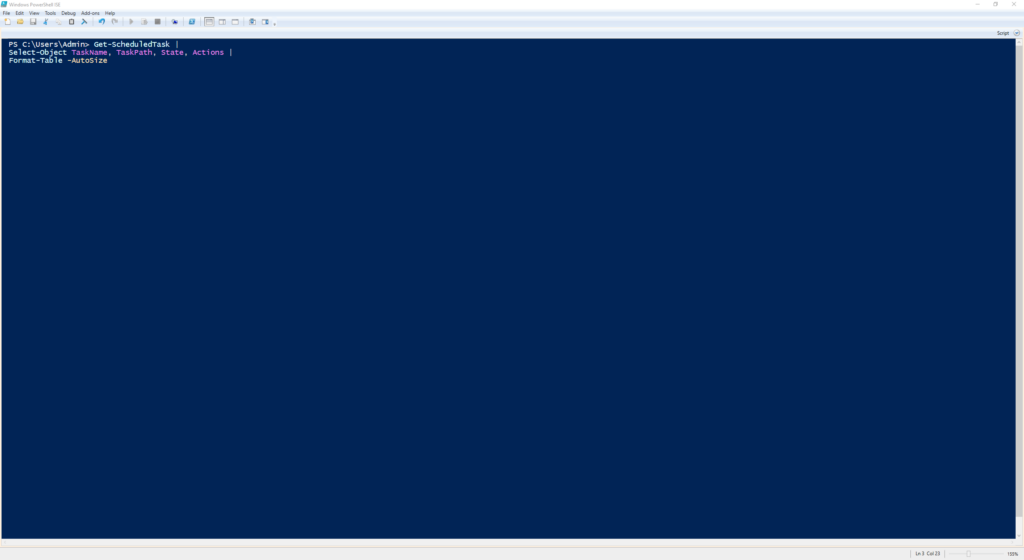
Lists all scheduled tasks and the commands they run.
- Common method for persistence and privilege escalation
- Useful for identifying tasks created by attackers
- Lets you quickly review task names and associated actions
What It Does:Get-ScheduledTask – Lists all tasks on the systemSelect-Object TaskName, TaskPath, State, Actions – Shows task name, location, status, and what it executesFormat-Table -AutoSize – Makes the output easier to read
Check Autoruns via Registry and File Locations
Get-CimInstance -ClassName Win32_StartupCommand |
Select-Object Name, Command, Location |
Format-Table -AutoSize
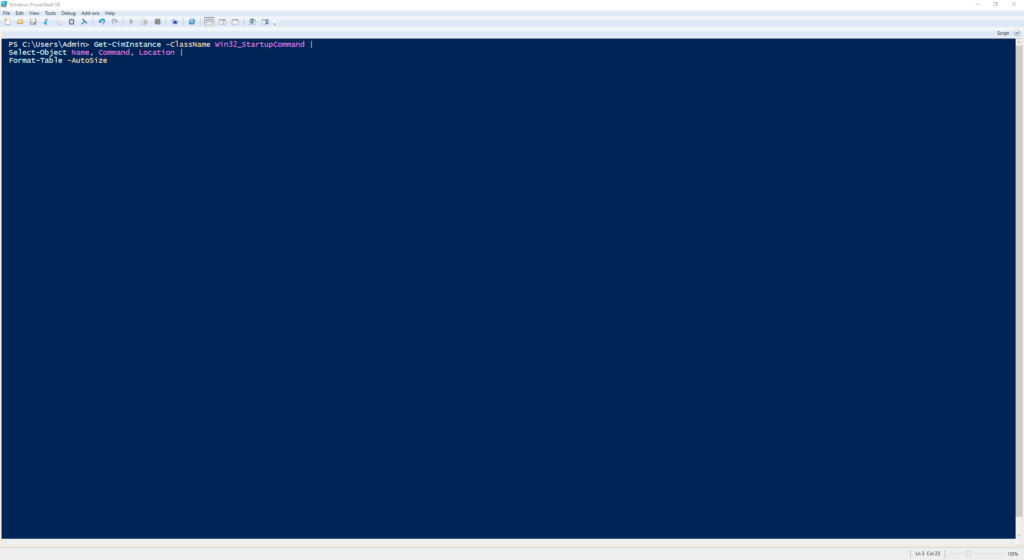
Returns autorun programs configured via registry keys or special folders.
- Often used by malware to ensure persistence
- Similar to Autoruns utility but scriptable via PowerShell
- Displays the name, location, and exact command
What It Does:Get-CimInstance -ClassName Win32_StartupCommand – Queries startup locations
Select-Object Name, Command, Location
Format-Table -AutoSize – Formats into a readable table
List PowerShell Execution History
Get-Content (Get-PSReadlineOption).HistorySavePath | Select-String .
Lists all previously run PowerShell commands by the current user.
- Useful for reviewing recent attacker activity
- Great for forensic review during compromise
- Reveals what scripts or commands have been typed in
Side Note: This one must be run through a Powershell terminal, not in ISE. For ISE use (Get-History).CommandLine
What It Does:Get-PSReadlineOption – Finds the path of the PowerShell history fileGet-Content – Reads that fileSelect-String . – Returns all lines containing text (i.e., all command history)
List Local Administrators on the Machine
Get-LocalGroupMember -Group "Administrators"
Lists all members of the local Administrators group.
- Critical for auditing who has elevated access
- Can help detect privilege abuse or persistence via hidden accounts
- Useful during both incident response and proactive hardening
What It Does:Get-LocalGroupMember – Lists all members of a specific group-Group "Administrators" – Targets the built-in local admin group

