Why QR codes?
When we talk about phishing and malicious links, most people think of sketchy emails or suspicious text messages. But there’s a threat that often flies under the radar: QR codes.
Originally designed as a convenient way to direct users to websites, download apps, or make payments; QR codes have become a common sight in restaurants, advertisements, parking meters, and even at your local coffee shop. But, that convenience comes with a risk: QR codes can just as easily lead to malicious content as they can to a restaurant menu. After all, at its core, a QR code is simply data encoded visually as a two-dimensional barcode. Most commonly, that data is a URL, but it can also be plain text, Wi-Fi credentials, contact info, crypto wallet addresses, or even commands depending on where it’s used.
How Attackers Abuse QR Codes
The problem with QR codes is simple: You can’t visually “read” where they point before scanning. Unlike a traditional hyperlink where you can hover and inspect the destination, QR codes hide the link behind a pattern of squares. This makes QR codes an attractive tool for attackers. They can direct unsuspecting users to:
- Phishing websites that look like legitimate login pages.
- Malware downloads that install spyware or remote access tools.
- Fake payment portals designed to steal credit card information.
- Credential harvesting sites disguised as secure company portals.
Real-World Examples
Here are some real-world examples. Keep in mind that QR dangers are not limited to the following:
- Fake parking meter QR codes that redirect users to fraudulent payment sites.
- QR codes placed over legitimate ones on public posters or flyers.
- Phishing emails encouraging users to scan a QR code instead of clicking a link, often bypassing email link filters.
How to Protect Yourself
✅ Always verify the source of the QR code. Did it come from a trusted company, or could someone have slapped a sticker over the original?
✅ Use a QR scanner app that previews the URL before opening it (some smartphone cameras have this feature built-in).
✅ Be extra cautious when a QR code asks you to enter login credentials or payment information.
✅ Avoid scanning codes from random emails, texts, or social media posts, just like you would avoid clicking suspicious links.
✅ Check for tampering. Is the QR code stickered over another code? Is it peeling off?
Here is a simple example I took on my phone of a generated QR code:
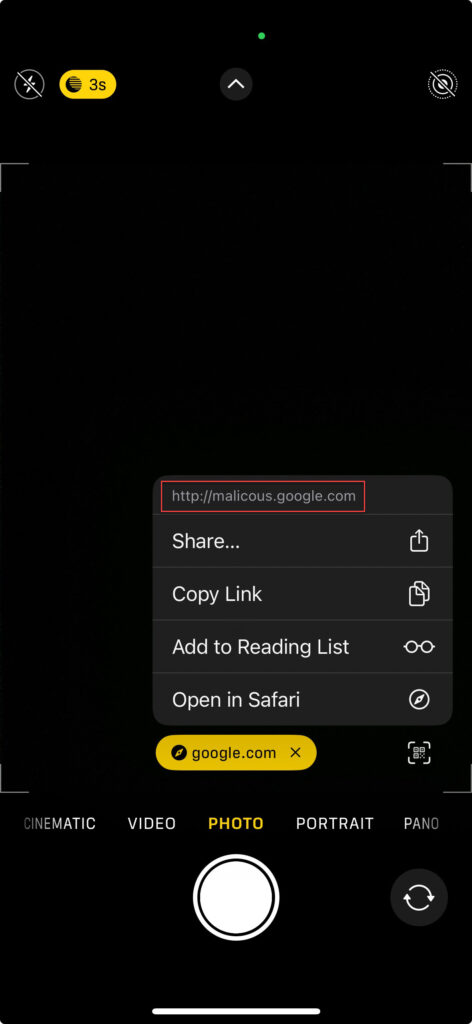
As shown in the example, if you tap the icon resembling a QR code in the bottom-right corner, the link will be displayed before opening. If the link is too long to read easily, you can copy and paste it into a note-taking app for closer inspection. This demonstration is on an iPhone, I don’t have an Android example on hand, but I believe the process is similar on most devices.
Stay Aware, Stay Safe
Attackers are always looking for ways to exploit our habits. While many of us know not to click unknown links, QR codes have become a modern loophole in our caution. Stay aware, question before you scan, and remember: not every QR code is as innocent as it looks.

